
DDOS PROTECTION
THE PROTECTION YOU NEEDED
Le attuali soluzioni hardware presenti sul mercato per la mitigazione di attacchi DDoS hanno costi generalmente molto elevati. Per riuscire a offrire un prodotto estremamente competitivo, abbiamo quindi deciso di sviluppare internamente la tecnologia di cui abbiamo bisogno. Il nostro sistema di mitigazione ci consente di filtrare anche gli attacchi più avanzati, analizzando il traffico in ingresso e utilizzando tecnologie all’avanguardia come XDP per uno scrubbing ad alte prestazioni.
Since 2015, we've developed our in-house DDoS protection system. Our core protection is now delivered via multiple 100Gbit NIC servers in load-balanced configurations powered by XDP. We’ve also implemented a routing-layer pre-filtering system for advanced traffic scrubbing.
Warning: Due to the connection-less nature of UDP, this protocol requires specific protection measures, and the defense approach must take into account the hosted application. For this reason, UDP protection falls under our "advanced protection" tier.
| FEATURES | PROTECTION | ADVANCED PROTECTION | CUSTOM PROTECTION |
|---|---|---|---|
| Offer Validity | VPS, DDoS-Protected VPS, Semi-Dedicated Servers, Dedicated Servers | VPS, DDoS-Protected VPS, Semi-Dedicated Servers, Dedicated Servers | All |
| DDoS Protection | Always-On | Always-On | Always-On |
| Price | Free | 14€/mouth | On-demand |
| Max packets per second (PPS) | Unlimited | Unlimited | Unlimited |
| Redundant Firewalls | 2M PPS | 960M PPS | On-demand |
| Redundant firewalls | Yes | Yes | Yes |
| Protected Attacks | TCP SYN/ACK/FIN/RST/PSH (Spoofed/Non-Spoofed), ICMP/UDP/TCP Flood, DNS, SNMP, RIP, NTP, LDAP Reflection amplification | Protection + UDP TS3-optimized + UDP GTA:V Roleplay, Rust, MCPE, DayZ Standalone, ARK Survival Evolved + UDP avanzata (contattaci) |
+ Custom L7 |
- Offer ValidityVPS, DDoS-Protected VPS, Semi-Dedicated Servers, Dedicated Servers
- DDoS ProtectionAlways-On
- PriceFree
- Max packets per second (PPS)Unlimited
- Redundant Firewalls2M PPS
- Redundant firewallsYes
- Protected AttacksTCP SYN/ACK/FIN/RST/PSH (Spoofed/Non-Spoofed), ICMP/UDP/TCP Flood, DNS, SNMP, RIP, NTP, LDAP Reflection amplification
- Offer ValidityVPS, DDoS-Protected VPS, Semi-Dedicated Servers, Dedicated Servers
- DDoS ProtectionAlways-On
- Price14€/mouth
- Max packets per second (PPS)Unlimited
- Redundant Firewalls960M PPS
- Redundant firewallsYes
- Protected AttacksProtection
+ UDP TS3-optimized
+ UDP GTA:V Roleplay, Rust, MCPE, DayZ Standalone, ARK Survival Evolved + UDP avanzata (contattaci)
- Offer ValidityAll
- DDoS ProtectionAlways-On
- PriceOn-demand
- Max packets per second (PPS)Unlimited
- Redundant FirewallsOn-demand
- Redundant firewallsYes
- Protected Attacks+ Custom L7

Semplice ed intelligente
ServerEasy operates its own network with sufficient bandwidth for attack mitigation, regardless of origin. This ensures service continuity for our clients, even during active attacks.

Protezione base e avanzata
All services include Basic Anti-DDoS Protection by default. The Basic Protection uses a preset configuration, while the Advanced Protection allows custom rule profiles tailored to your needs.
Best-in-class Anti-DDoS infrastructure
Regardless of your project's size or type (VPS, Dedicated Server, cloud infrastructure, IP Transit), Anti-DDoS protection is always available. To maintain uninterrupted service quality during an attack, no action is required – protection is fully automated and mitigation is always active.
- 1.2 Tbps/960 Mpps attack filtering capacity;
- Attack detection and ultra-fast malicious traffic mitigation;
- Unlimited protection at no extra costregardless of attack volume;
- 24/7 Mitigation, for the full attack duration coverage;
- Proven reliability in defending infrastructure from VPS to dedicated servers;
- Next-Gen Optimized Infrastructure delivering premium performance;
- Custom Configuration for tailored, maximum-efficiency protection.
Come viene gestito un attacco DDoS su ServerEasy
1. Detection
Security always begins with attention to detail. We continuously monitor traffic to identify every potential anomaly. Even a small spike could signal a DDoS attack. That's why we employ advanced technologies that analyze traffic behavior in real time, enabling immediate threat detection.


2. Response
Once the threat is detected, our system automatically enforces the necessary rules to block malicious traffic before it reaches your servers. This means your services continue operating normally—without disruption—even during mitigation.
3. Filtering
Not all traffic is equal—our mission is to never disrupt legitimate traffic. Thanks to our advanced firewalls, we precisely identify and filter only malicious traffic, allowing legitimate flows to pass unimpeded. This way, we protect what needs guarding without blocking what works.

4. Analysis
After every attack, we take time to thoroughly analyze the incident. We verify the effectiveness of countermeasures implemented and identify potential areas for improvement. This approach allows us to continuously strengthen our protection.
Enhances security and provides real-time control
Through your client portal, access a comprehensive security tool designed for effortless protection management. Select from multiple defense modes, monitor live traffic patterns, and instantly detect anomalies while distinguishing legitimate from malicious activity. Our system provides complete network security control without complexity, giving you real-time visibility and response capabilities at your fingertips.
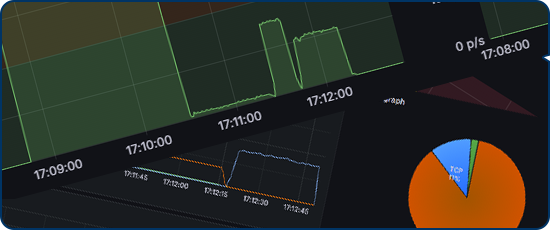

Advanced application-layer protection
In some cases, generic protection may not be enough. Targeted attacks often exploit specific vulnerabilities in application logic, bypassing traditional firewalls and IDS/IPS systems to compromise critical infrastructure. We offer advanced TCP/UDP application protection, including for real-time services like games, ~~effectively~~ defending against sophisticated targeted attacks. Our solutions ensure operational continuity, performance, and security—even in complex, large-scale scenarios. Each profile is meticulously tailored to your service’s unique requirements, guaranteeing uninterrupted security, performance, and uptime ~~under all attack conditions~~. For custom applications, we develop dedicated protection profiles with your team.


