While most DDoS mitigation hardware carries premium pricing, we built our own system to reduce costs without compromising power. It combats advanced attacks via real-time traffic analysis and XDP-based high-speed scrubbing.

DDOS PROTECTION
ENTERPRISE-GRADE DEFENSE, ON DEMAND
DDoS Protection
Since 2015, we have developed our in-house DDoS protection system.
Our Core Protection is currently delivered through multiple 100Gbit NIC servers in XDP-based load balancing. We have also developed a routing-level pre-filtering system.
Warning: Due to the connection-less nature of UDP, this protocol requires specific safeguards and generally needs protection tailored to the hosted application. For this reason, UDP protection falls under “Advanced Protection“.
Protezione DDoS
While most DDoS mitigation hardware carries premium pricing, we built our own system to reduce costs without compromising power. It combats advanced attacks via real-time traffic analysis and XDP-based high-speed scrubbing.
Since 2015, we have developed our in-house DDoS protection system.
Our Core Protection is currently delivered through multiple 100Gbit NIC servers in XDP-based load balancing. We have also developed a routing-level pre-filtering system.
Warning: Due to the connection-less nature of UDP, this protocol requires specific safeguards and generally needs protection tailored to the hosted application. For this reason, UDP protection falls under “Advanced Protection“.
Protezione DDoS
While most DDoS mitigation hardware carries premium pricing, we built our own system to reduce costs without compromising power. It combats advanced attacks via real-time traffic analysis and XDP-based high-speed scrubbing.
Since 2015, we have developed our in-house DDoS protection system.
Our Core Protection is currently delivered through multiple 100Gbit NIC servers in XDP-based load balancing. We have also developed a routing-level pre-filtering system.
Warning: Due to the connection-less nature of UDP, this protocol requires specific safeguards and generally needs protection tailored to the hosted application. For this reason, UDP protection falls under “Advanced Protection“.
| FEATURES | PROTECTION | ADVANCED PROTECTION | CUSTOM PROTECTION |
|---|---|---|---|
| Offer Validity | VPS, DDoS-Protected VPS, Semi-Dedicated Servers, Dedicated Servers | VPS, DDoS-Protected VPS, Semi-Dedicated Servers, Dedicated Servers | All |
| DDoS Protection | Always-On | Always-On | Always-On |
| Price | Free | 14€/mouth | On-demand |
| Number and duration of attacks | Unlimited | Unlimited | Unlimited |
| Max packets per second (PPS) | 2M PPS | 960M PPS | On-demand |
| Redundant Firewalls | Yes | Yes | Yes |
| Protected Attacks |
TCP SYN/ACK/FIN/RST/PSH (Spoofed/Non-Spoofed) ICMP/UDP/TCP Flood DNS, SNMP, RIP, NTP, LDAP Reflection amplification |
All Base Protection + UDP TS3-optimized + UDP GTA:V Roleplay, Rust, MCPE, DayZ Standalone, ARK Survival Evolved + Advanced UDP (Contact Us) |
+ Customs L7 |

Simple and Smart
ServerEasy manages its own network with sufficient bandwidth to mitigate attacks, regardless of their origin. This allows us to guarantee uninterrupted service to our clients, even during an ongoing attack.

Basic and Advanced Protection
All services come with Basic Anti-DDoS Protection enabled by default, featuring a preset configuration. Advanced Protection offers customizable security profiles to address specific requirements.

Simple and Smart
ServerEasy manages its own network with sufficient bandwidth to mitigate attacks, regardless of their origin. This allows us to guarantee uninterrupted service to our clients, even during an ongoing attack.

Basic and Advanced Protection
All services come with Basic Anti-DDoS Protection enabled by default, featuring a preset configuration. Advanced Protection offers customizable security profiles to address specific requirements.
The Ultimate Anti-DDoS Infrastructure
Regardless of project scale or type – whether VPS, Dedicated Server, cloud infrastructure, or IP Transit – Anti-DDoS protection is always available.
To ensure uncompromised service quality during attacks, no manual intervention is required: mitigation operates 24/7 with zero downtime.
- 1,2Tbps/960Mpps filtering capacity;
- Instant attack detection and ultra-fast malicious traffic scrubbing;
- Unlimited Protection – No hidden costs, regardless of attack size;
- 24/7 Mitigation – Full attack duration coverage;
- Proven Reliability defending all infrastructures (VPS to dedicated servers);
- Next-Gen Optimizedinfrastructuredelivering premium performance;
- Custom Configuration for tailored, maximum-efficiency protection.
The Ultimate Anti-DDoS Infrastructure
Regardless of project scale or type – whether VPS, Dedicated Server, cloud infrastructure, or IP Transit – Anti-DDoS protection is always available.
To ensure uncompromised service quality during attacks, no manual intervention is required: mitigation operates 24/7 with zero downtime.
- 1,2Tbps/960Mpps filtering capacity;
- Instant attack detection and ultra-fast malicious traffic scrubbing;
- Unlimited Protection – No hidden costs, regardless of attack size;
- 24/7 Mitigation – Full attack duration coverage;
- Proven Reliability defending all infrastructures (VPS to dedicated servers);
- Next-Gen Optimizedinfrastructuredelivering premium performance;
- Custom Configuration for tailored, maximum-efficiency protection.
The Ultimate Anti-DDoS Infrastructure
Regardless of project scale or type – whether VPS, Dedicated Server, cloud infrastructure, or IP Transit – Anti-DDoS protection is always available.
To ensure uncompromised service quality during attacks, no manual intervention is required: mitigation operates 24/7 with zero downtime.
- 1,2Tbps/960Mpps filtering capacity;
- Instant attack detection and ultra-fast malicious traffic scrubbing;
- Unlimited Protection – No hidden costs, regardless of attack size;
- 24/7 Mitigation – Full attack duration coverage;
- Proven Reliability defending all infrastructures (VPS to dedicated servers);
- Next-Gen Optimizedinfrastructuredelivering premium performance;
- Custom Configuration for tailored, maximum-efficiency protection.
How We Handle DDoS Attacks at Servereasy.it

1. Detection
Security always begins with meticulous attention to detail. We constantly monitor network traffic to identify even the most subtle anomalies – because the slightest irregularity could signal an emerging DDoS attack. This is why we employ cutting-edge technologies that analyze traffic behavior in real time, enabling immediate threat detection and response.

2. Response
The moment an issue is detected, our system automatically enforces all necessary rules to block malicious traffic before it ever reaches your servers. This means your services continue operating normally without interruption – even during active mitigation.
3. Filtering
Non tutto il traffico è uguale, il nostro compito è non interrompere il traffico legittimo. Grazie ai nostri firewall, siamo in grado di riconoscere e filtrare solo il traffico malevolo, lasciando passare quello legittimo senza impattare sull’esperienza degli utenti. Così proteggeremo ciò che serve, senza bloccare ciò che funziona.

4. Analytics
Dopo ogni attacco, ci prendiamo il tempo per analizzare a fondo ciò che è accaduto. Verifichiamo l’efficacia delle contromisure adottate e individuiamo eventuali margini di miglioramento. Questo approccio ci permette di rafforzare continuamente la nostra protezione.
How We Handle DDoS Attacks at Servereasy.it

1. Detection
Security always begins with meticulous attention to detail. We constantly monitor network traffic to identify even the most subtle anomalies – because the slightest irregularity could signal an emerging DDoS attack. This is why we employ cutting-edge technologies that analyze traffic behavior in real time, enabling immediate threat detection and response.

2. Response
The moment an issue is detected, our system automatically enforces all necessary rules to block malicious traffic before it ever reaches your servers. This means your services continue operating normally without interruption – even during active mitigation.
3. Filtering
Not all traffic is the same our job is to never disrupt legitimate traffic.Thanks to our advanced firewall systems, we can precisely identify and filter only malicious traffic, allowing legitimate requests to flow uninterrupted. This ensures full protection without compromising user experience.
We safeguard what needs defending, without blocking what works.
4. Analysis
After every attack, we dedicate time to fully analyze what occurred. We assess the effectiveness of the countermeasures taken and identify any areas for improvement. This approach allows us to continuously strengthen our protection systems.
How We Handle DDoS Attacks at Servereasy.it

1. Detection
Security always begins with meticulous attention to detail. We constantly monitor network traffic to identify even the most subtle anomalies – because the slightest irregularity could signal an emerging DDoS attack. This is why we employ cutting-edge technologies that analyze traffic behavior in real time, enabling immediate threat detection and response.
2. Response
The moment an issue is detected, our system automatically enforces all necessary rules to block malicious traffic before it ever reaches your servers. This means your services continue operating normally without interruption – even during active mitigation.
3. Filtering
Not all traffic is the same our job is to never disrupt legitimate traffic.Thanks to our advanced firewall systems, we can precisely identify and filter only malicious traffic, allowing legitimate requests to flow uninterrupted. This ensures full protection without compromising user experience.
We safeguard what needs defending, without blocking what works.


4. Analysis
After every attack, we dedicate time to fully analyze what occurred. We assess the effectiveness of the countermeasures taken and identify any areas for improvement. This approach allows us to continuously strengthen our protection systems.
Enhance security and gain real-time control
Through the customer portal, you access a powerful yet intuitive tool to manage your protection seamlessly. Switch between security modes, monitor live traffic, and instantly spot anomalies all while maintaining clear separation between legitimate and malicious traffic. Every feature is designed to give you complete network security control without added complexity.
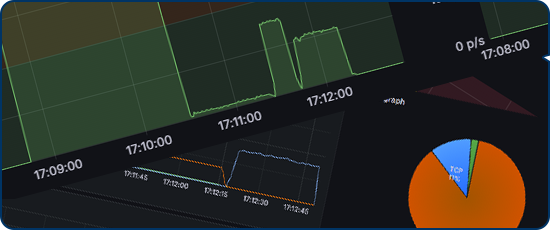
Enhance security and gain real-time control
Through the customer portal, you access a powerful yet intuitive tool to manage your protection seamlessly. Switch between security modes, monitor live traffic, and instantly spot anomalies all while maintaining clear separation between legitimate and malicious traffic. Every feature is designed to give you complete network security control without added complexity.

Enhance security and gain real-time control
Through the customer portal, you access a powerful yet intuitive tool to manage your protection seamlessly. Switch between security modes, monitor live traffic, and instantly spot anomalies all while maintaining clear separation between legitimate and malicious traffic. Every feature is designed to give you complete network security control without added complexity.


Advanced L7 Protection
Sometimes generic protection isn’t enough. Targeted attacks frequently exploit specific vulnerabilities in application logic, bypassing traditional firewalls and compromising systems. We deliver advanced TCP/UDP application protection – including for gaming platforms – to effectively defend against these sophisticated threats. Our solutions ensure operational continuity, performance, and security even in complex attack scenarios.
Every protection profile is custom-designed to match your service’s unique requirements, guaranteeing security, performance, and uninterrupted operation under all conditions. For custom applications, we can develop specialized protection profiles tailored to your exact needs.

Advanced L7 Protection
Sometimes generic protection isn’t enough. Targeted attacks frequently exploit specific vulnerabilities in application logic, bypassing traditional firewalls and compromising systems. We deliver advanced TCP/UDP application protection – including for gaming platforms – to effectively defend against these sophisticated threats. Our solutions ensure operational continuity, performance, and security even in complex attack scenarios.
Every protection profile is custom-designed to match your service’s unique requirements, guaranteeing security, performance, and uninterrupted operation under all conditions. For custom applications, we can develop specialized protection profiles tailored to your exact needs.

Advanced L7 Protection
Sometimes generic protection isn’t enough. Targeted attacks frequently exploit specific vulnerabilities in application logic, bypassing traditional firewalls and compromising systems. We deliver advanced TCP/UDP application protection – including for gaming platforms – to effectively defend against these sophisticated threats. Our solutions ensure operational continuity, performance, and security even in complex attack scenarios.
Every protection profile is custom-designed to match your service’s unique requirements, guaranteeing security, performance, and uninterrupted operation under all conditions. For custom applications, we can develop specialized protection profiles tailored to your exact needs.


